Which of the Following Is Best Used With Vulnerability Assessments
Vulnerability and Risk Assessment DRAFT. Vulnerability assessment is the process of defining identifying classifying and prioritizing vulnerabilities in systems applications and networks.

Vulnerabilty Assessment Itgid It Governance Indonesia
Which of the following statements best describes how risk and vulnerability assessment information is used to identify mitigation opportunities.

. Correct answer of the above question is. Which of the following is a graphical interface for Nmap that is typically used during the scanning phase of the ethical hacking process. At a tactical level the vulnerability assessment process can help.
Using the open standards tripwire IP360 enables the integration of risk management and vulnerability into multiple processes of the business. A vulnerability assessment tests some or all of your systems and generates a detailed vulnerability report. Run a port scan.
Which of the following aims to integrate the defensive tactics and controls from the Blue Team with the threa. Which of the following best describes how inspection services contribute to the recovery process. Tripwire IP360 is the worlds foremost vulnerability assessment solution that is used by various agencies and enterprises to administrate their security risks.
Vulnerability assessments provide information about all the hazards that are likely to occur. Measurement of a communitys response capabilities. Which of the following is best used with vulnerability assessments.
Detailed and accurate data that can be used for damage assessment documentation. Q18 The type of assessment that is best used to identify classify and prioritize vulnerabilities. Question Posted on 19 Jul 2021.
In addition an ever-increasing number of companies depend on technology to carry out their daily operations but cyber threats like ransomware can. Vulnerability analysis also known as vulnerability assessment is a process that defines identifies and classifies the security holes in a computer network or communications infrastructure. The following best describes the difference between a risk assessment and a vulnerability assessmentRisk assessments consider how each potential hazard will affect critical infrastructure and key resources.
Which of the following best describes the information that risk and vulnerability assessments can provide. A vulnerability assessment is a process so complicated that it often requires a comprehensive approach. Detailed and accurate data that can be used for damage assessment documentation C.
Which of the following best finds uncommon and eccentric issues. A Penetration Testing b Threat Modeling c Bug Bounty d Vulnerability Assessment e Red Team Assessment. Which of the following best describes the information that risk and hazard vulnerability assessments can provide.
Measurement of a communitys response capabilities D. Which of the following best describes the information that risk and hazard vulnerability assessments can provide. Prescribed response actions for each hazard identified in the analysis B.
Detailed and accurate data that can be used for damage assessment documentation. The information is used to assign functional roles and responsibilities within the public works agency. Deliberate CBRN vulnerability assessment is the application of the complete vulnerability assessment process when time is not critical.
Which type of vulnerability assessments software can check for weak passwords on the network. Measurement of a communitys response capabilities. Testing analysis assessment and remediation.
This would mean that a multiple sub-assessments are to be executed each of which spanning different areas within the evaluated organizations IT system in order the final analysis to be exhaustive enough to produce meaningful results. During the vulnerability assessment any known vulnerabilities or bugs will be flagged and identified by. Deliberate vulnerability assessments primarily use experience and brainstorming to identify threatsvulnerabilities and develop reduction measures and controls and are therefore most effective when done in a group.
This report can then be used to fix the problems uncovered to avoid security breaches. It provides an organization with the needed visibility into the risks that exist concerning external threats designed to take advantage of vulnerabilities. Inspection services allow for accurate risk and vulnerability assessments used in recovery planning.
Penetration testing is also called as ethical hacking. Inspection services determine the proper course of action for damaged buildings or facilities. The _____ is a form of TCP scanning that is less intrusive on the target host.
A process that aims to gain information about a system without directly engaging with the system is known as _______________ View-5629. ADS Posted In. An evaluation of how the hazards identified could affect your community.
Vulnerability identification testing The objective of this step is to draft a comprehensive list of an applications vulnerabilities. Important Topics Security Assessment. Of the following which is the best way for a person to find out what security holes exist on the network.
The security scanning process consists of four steps. Select the appropriate answer from below options. Grey Box Testing Black Box Testing White Box Testing.
The information prescribes a plan of action that can be taken after the impact of hazard events. Prescribed response actions for each hazard identified in the analysis.

Vulnerabilty Assessment Itgid It Governance Indonesia

Cyber Security Vulnerability Assessment Tools Cyber Security Awareness Vulnerability Cyber Security
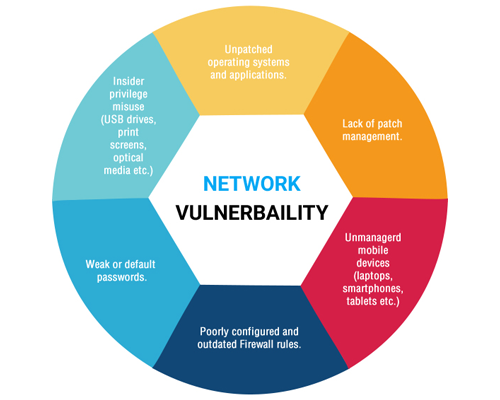
What Is Network Vulnerability Vulnerability Assessment Report
Comments
Post a Comment